Dynamic Port Forwarding with SOCKS over SSH is probably the easiest and cheapest secure method to connect a client application to a remote host over a preferred port.
This method allows an application on a client computer to make request to a local port, then the requests are forwarded to a remote host, which processes the requests and returns the data back to the client. This is very similar to a simple proxy, with the exception that in a proxy set up the application sends data directly to the remote host, while in this configuration we have an emulated local SOCKS server that handles the requests first and then directs them to the remote computer… oh yeah… and the network traffic is encrypted.
Dynamic Port Forwarding over SSH is in a way a simple alternative to VPN.
Why would anyone need this? Two main reasons immediately come to mind. First, if you are on a public, non secure, non trusted, unencrypted network (for example at the local coffee shop) you can use this method to securely connect to a remote host and have your network traffic encrypted and thus protect your data and privacy. Second, if you need to bypass local network restrictions and monitoring services. A good example here is circumventing surf control restrictions. In most cases, surf control is implemented by monitoring the traffic and examining the tcp/ip packets over port 80. By using Dynamic Port Forwarding over SSH, we channel http traffic through a different port and furthermore all http requests/responses are encrypted via ssh and thus cannot be examined or filtered.
Now let’s see how it is done.
Remote Host Setup.
A remote host is needed that will receive and process the requests from the client. Any computer or device can be the remote host as long as it runs ssh. In this respect any Linux box is ideal for that purpose.
From a practical standpoint, your home router is probably one of the best candidates for being your remote host. You need to run open source software on it, like OpenWRT, DD-WRT, Tomato, etc. and have ssh enabled on it. If you are still running the original firmware that you router came with, you are only using a fraction of the hardware’s capabilities and you are missing out on a lot of great features.
If you plan on using a computer on your home network as the remote ssh host, do not forget to set up the port forwarding on your router accordingly.
Client Setup.
If your client is a Linux box, you hardly have to set up anything. All you have to do is connect to the remote host with the following command:
ssh –D port_number user_name@remote_host (for example: ssh –D 8080 dimitar@72.134.54.23)
And then the only thing that is left is to configure your application to use SOCKS. Look at the Firefox setup below as an example (Step 7).
If your client is a Windows box, you have to install an ssh client. PuTTY is a good ssh client for Windows and it is free:
Step 1. Download PuTTY.
Step 2. Open up PuTTY and put in the host IP address or domain name. Leave the port as the default 22 and give the connection a name under “Saved Sessions” and click “Save”:
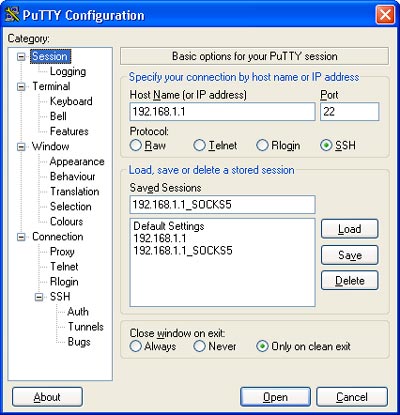
Step 3. Click the “SSH” on the left hand side under “Connections” and make sure that the “Preferred SSH protocol version” is set to 2.
Step 4. Click on “Auth” and select “Allow agent forwarding”:
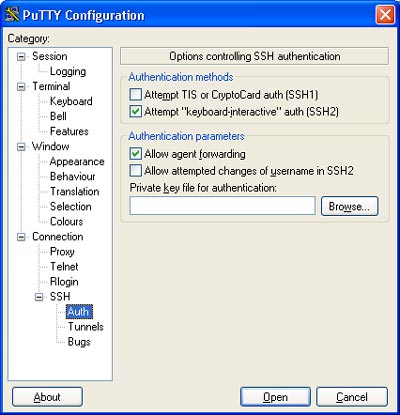
Step 5. Go to “Tunnels” and enter the port in the “Source Port” field, select the “Dynamic” radio button and click the “Add” button. Here optionally you can check “Enable X11 forwarding”, which will come in handy if you want to run graphical applications from the remote host. For this piece to work though, you will need an X11 client running on your Windows client, like Cygwin, Reflections X, Humming Bird, etc., but this is beyond this discussion.
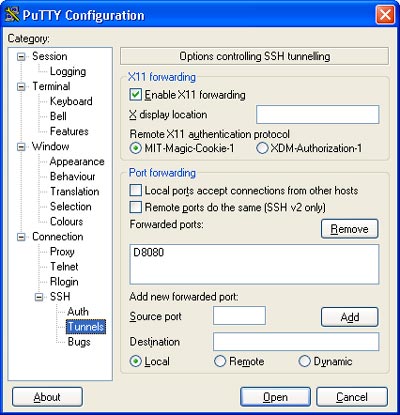
Step 6. Click “Session” on the top left to go back to the first screen and save your setting.
Step 7. Now you are ready to configure your application to use the Dynamic Port Forwarding with SOCKS. For this exercise we will configure Firefox. Open Firebox’s “Options” dialog (called “Preferences” if running on Linux) and go to “Advanced” and then “Network”, hit the “Settings” button under “Connection”. In the window that pops up select “Manual proxy configuration”, enter localhost for “SOCKS host” and the port number (8080 for this exercise). Select the “SOCKS v5” radio button and enter localhost, 127.0.0.1 in the “No Proxy for” box:
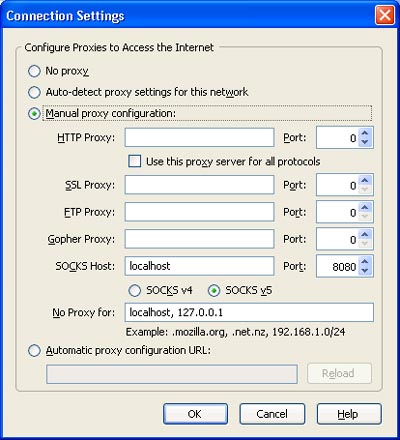
Now when you browse the internet with Firefox, all the traffic will be directed to the local SOCKS proxy server on port 8080, then the packest will be encrypted and forwarded over ssh on port 22 to the remote host (you can alwasy change the default ssh port to any other port). It is important to notice, that the remote host will decrypt the packets from the client and then make the requests on port 80 without encryption.
If I want set up SSH tunnel to connect to a proxy.
For example: MyPC[192.168.1.2] -> SSHServer[108.84.147.1:22] -> PublicWebProxy[91.187.125.194:8080].
Is it possible? What settings I should make?
Pingback:Install SSH as socks proxy for dynamic port forwarding | Steve Constine
Hi,
Nice article. I wonder if it is possible to connect via the proxy to a server that is accessible via a tunnel.
For example, my server A has a tunnel on my server B
I connect to server B with dynamic port forwarding.
I redirect port 80 on my server B but I could not get access via the dynamic forwarding. Any idea?
Is it possibile to mage tunnel to sshd listening on custom port ? not 22 .. f.e. 3128 ?
@Tom,
Yes you can do that on any port including 3128. To do that you need to have your remote server configured so that the sshd is listing on port 3128 instead of the default 22.
Pingback:????? » 2015?4?10?gae goagent?????
Hi,
I have a remote server1(with application1 hosted) & remote server 2(application hosted 2).
I am able to tunnel to both the servers from my desktop and setup request and responses.
But now the question is, is there a way I can setup connectivity from Server1 to Server2 via by desktop. So request from server1 –> desktop(via) —> server2(request processed) —> server2 (sends response) –> desktop (via)–> server1(handles response)
These seeting can be applied using putty?.
Agent forwarding is not needed for this and should not be enabled – if the remote host is compromised, it can steal the user’s keys. (It is needed if you want to SSH to other hosts from the shell of the forwarder box, but setting up the proxy settings to use plink for the tunnel is safer and works better for that) (The agent never gets forwarded to to jump-host when done that way)