Chromecast devices are discoverable on the network via the mDNS protocol and that works well when all devices are on the same network. Things start to break down though if the Chromecast devices and the clients that would like to cast to them (phones, PCs, etc.) are on different subnets. In that case the clients cannot “see” the Chromecast devices to cast to.
The issue is that mDNS is a broadcast protocol and the mDNS packets have a TTL of 1, which means that they are not routable and they do not get propagated anywhere outside of the local subnet.
In order to fix this issue, we need to find a way to re-broadcast the mDNS packets from one subnet to the next. In pfSense we can do this with the Avahi package:
- Install Avahi
In pfSense, go to System -> Package Manager -> Available Packages, search for “Avahi” and then hit the “Install” button next to it.
- Configure Avahi
Go to Services -> Avahi
Enable the Avahi deamon, the action should be “Allow Interfaces” and make sure that all the desired interfaces and VLANs are listed in the “Interfaces” input box. Then enable the “Repeat mdns packets across subnets” option. That should open another block titled “Reflection Filtering”. In that box we need to put in the mDNS service names to be allowed to be replicated. Google Chrome devices use the _googlecast._tcp.local service name, so enter “_googlecast._tcp.local” in the “Service” box. If you have other services that you would like to allow advertising/discoverablility for (e.g. printers), hit the “Add” button and enter the desired service name in the next “Service” input box. Here is how this looks in my case:
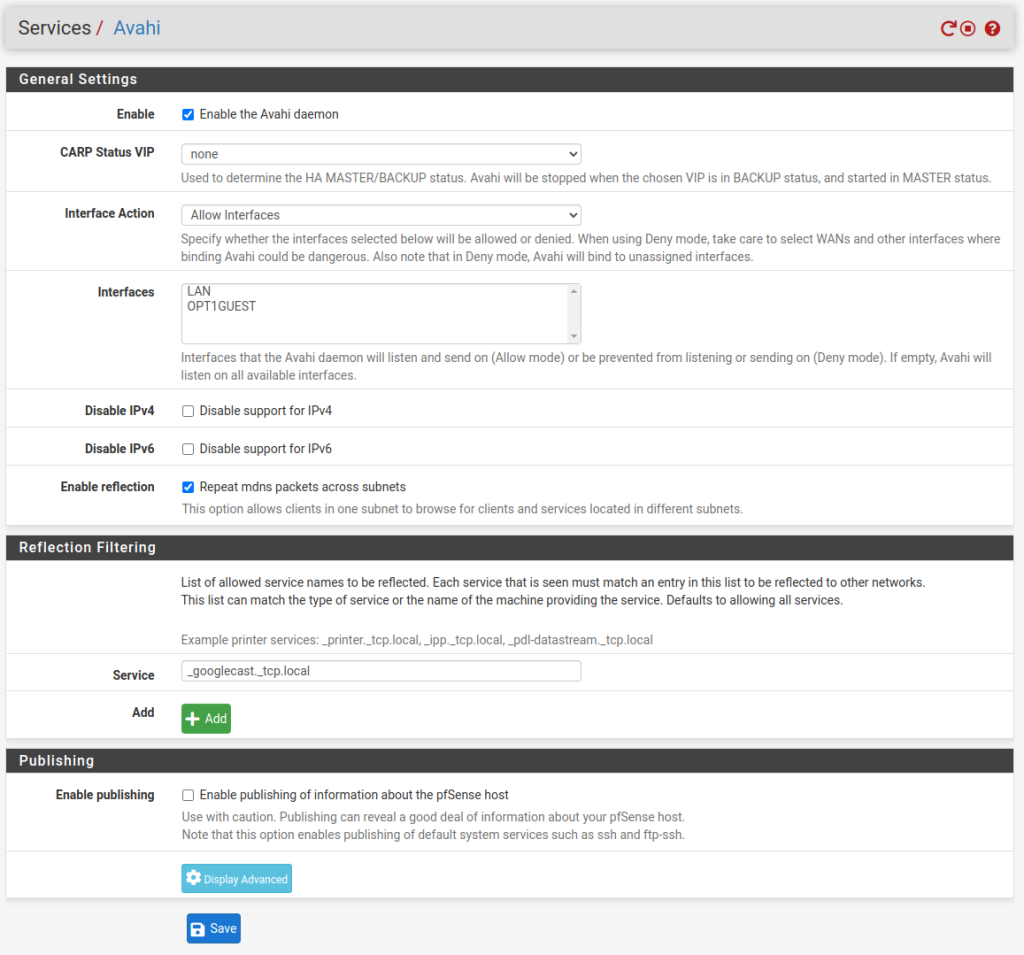
Once done, hit “Save” and then restart the service by clicking the restart red arrow button at the top right.
Now the Chromacast devices should be discoverable by the clients on your other networks. You should be able to cast different application content, like YouTube, Pocket Cast etc.
If you want to be able to video stream to the Chromecast devices from the other networks as well, for example casting devices screens or browser tabs, then the Chromecast devices need to be able to reach the source devices over TCP/5556 and TCP/5558.
To do that you need to add a rule to your interface where the Chromecast devices are on to allow them to reach the other network(s) over TCP on these two destination ports.
But first, it is better to create an alias with the two ports that later will be used by the new firewall rule. That is not mandatory and not the only way to do this, but in my opinion is a cleaner and more future proof option than the alternatives. It just makes things so much easier to read and maintain.
Go to Firewall -> Aliases -> Ports and the “Add” button. Give the alias a name and description and pick “ports” from the Type drop down, then enter the two ports and hit “Save”:
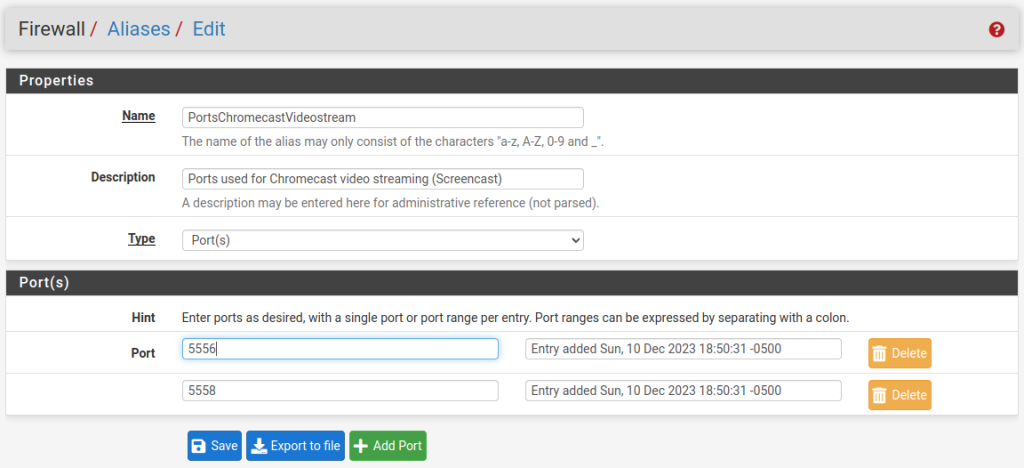
Now we are ready to add a firewall rule that will use this alias.
Go to Firewall -> Rules and pick the interface for the network/VLAN where your Chromecast devices reside and hit the “Add” button with the arrow pointing up in order to add a new rule at the top. In most cases there will be block rules following this rule, so we need to ensure that this rule will be reachable. In this new rule we could be very restrictive and specify the IPs of each individual Chromecast device in the source of this rule as well as specify individual IPs on the other networks that will be steaming the videos, but I think this is an overkill unless there is a specific concern or need. Having any source to any destination over these two ports will probably be all that is needed.
In my case, the interface for the Chromecast devices and other IoT devices is named “OPT1GUEST”. I have allowed any source on that network to reach all my private networks over TCP on these two ports:
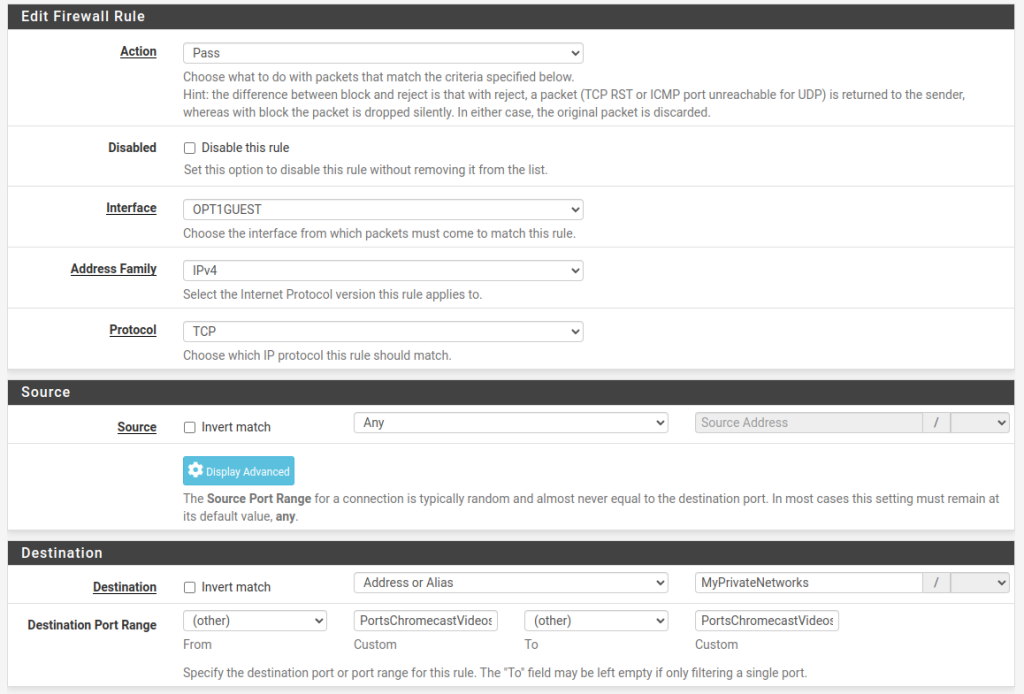
The “MyPrivateNetworks” above is an alias that contains the network ranges of all my private networks (you can pick “any” here in most cases) and the “PortsChromecastVideosPorts” is the alias we created above with the two ports defined.
Additional resources: Configuration document from Cisco on setting up mDNS service for Chromecast devices
Hello,
I am looking for the exact opposite of this. I want to prevent others from chromecasting on my device. I lost track of how many times some 1 has cast his music on my speakers. They are set to be private on google home but somehow it still happens…
I do not have a VLAN set up yet but since you are saying that this will actually prevent other people casting on my device I might as well put all my devices in a single VLAN.
Though it would be much better if I could allow only specific range of devices to chrome cast on this single device. Any hints for this? I tried to make a firewall rule to block all traffic to and from my speakers – this stopped me from being able to cast on it. Yet the rule to allow all traffic between my devices (set up as Alias via IPs) did not let me cast… I’m guessing this chromecast device 1st needs access to the internet before it starts accepting packets…
Hello, if you prevent abuse in cast for your devices, its possible use the avahi with deny rules, allowing only defined ips for casting. But, now, i’m trying implement the tutorial. Thanks.